Be honest: when you sign up for some website, do you just use the same email address / password? If so, you’re not alone – around three-quarters of people reuse the same passwords, even though most know they really shouldn’t.
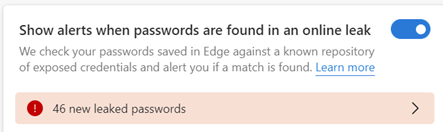
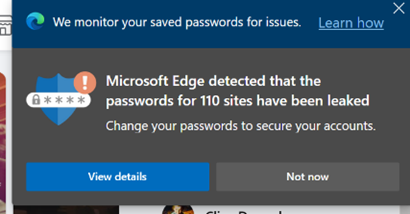
A CyberNews study of over 19 billion exposed passwords shows that many are weak and easy to guess, too – the most popular passwords for the last 15 years are, basically, “123456” and “password”. Some of the more high-profile security breaches have come about directly because of weak and compromised credentials.
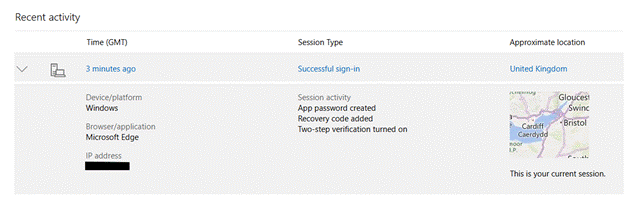
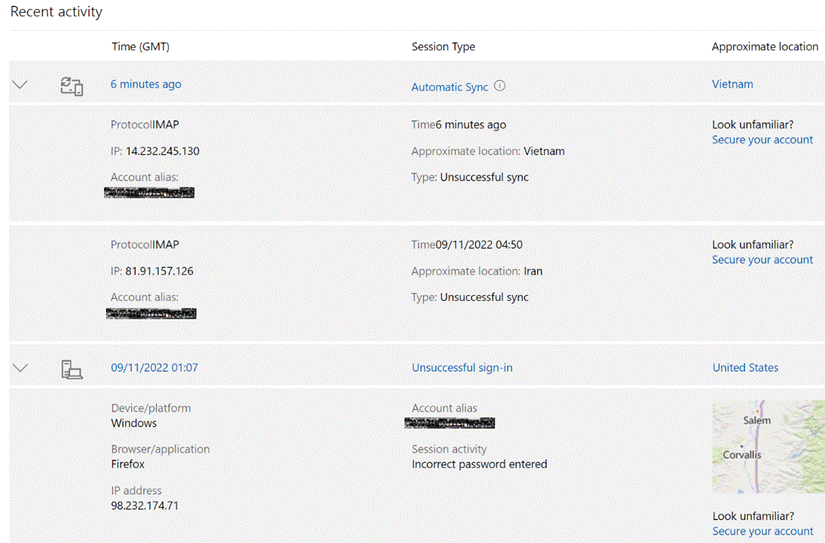
ToW has talked about passwords a bit in the distant past – #620, #656 in the old days, and most recently, #33 – Securing your Microsoft Account (MSA). If you haven’t done so already, go right now to that last link and set up Multifactor Autthentication (MFA) on your Microsoft Account.
Authenticator being Edged out
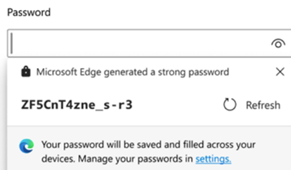
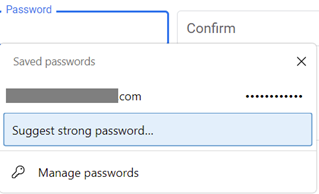
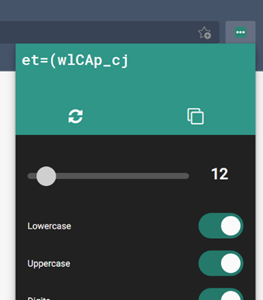
Like Google Chrome, Firefox and pretty much every modern browser, Microsoft’s Edge can offer to generate nice complex passwords for you. It also has a password store which can automatically fill your usernames & passwords next time you revisit websites, so you don’t need to remember them or write them down, and synchronise them between different devices logged in with the same ID.
In shock news bordering on marginal enshittification, Microsoft has decided to remove a useful component of the Authenticator app that it prefers to use for managing 2FA/MFA on its various types of logins.
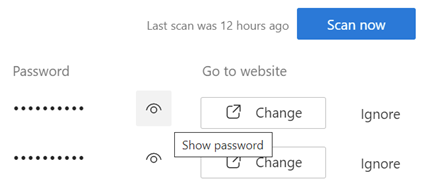
Thus far, if you have Authenticator set up with your Microsoft Account or an Entra ID, you can sync your passwords from the PC and be able to review them in the app, just as you would by going to Settings / Passwords options in the desktop Edge browser (or entering edge://wallet/passwords into the address bar).
This means that it can be handy to find a username/password when you’re mobile, in case you need to enter it manually, but also it allows Authenticator to provide an “autofill service” for other apps on your device, not just web pages. When you get unceremoniously signed out of an app just because it’s been automatically updated, the autofill service can recover and re-enter your username and password.
It’s this bit that is being yanked from Authenticator – for reasons unknown, other than “Microsoft is streamlining autofill”. Maybe nobody uses it? Maybe Microsoft would prefer anyone who does use Edge on their PC and who wants to access passwords while mobile, to be compelled to use Edge on their Phone also?
Similarly, Payment info that is synced from browser to Authenticator will be removed in July 2025.
The workaround (other than moving to a completely different password management system) is indeed to switch autofill provider on your phone to use Edge instead (having first installed it and synced it with your ID, if you haven’t already). In mitigation, the mobile versions of the browser are pretty good, and if you do use Edge on the PC or Mac, it makes sense to sync stuff across to your phone as well.
The password autofill is pretty much indistinguishable when using Edge in place of Authenticator. The UX for password management, however, isn’t so good (go into mobile Edge, Settings, and look for Passwords) but maybe that’s the price of progress?